Aptamer Technology
Aptamer
- Single-stranded oligonucleotides that specifically
bind to targets in three-dimensional structures -
Aptamers are single-stranded oligonucleotide (DNA, RNA) that specifically bind to target molecules (e.g. proteins, small molecules) like antibodies, and they are extensively used for the development of research tools, diagnosis and therapeutics.
In particular, antibody-drug conjugate (ADC)-based technology has difficulty in controlling the conjugation of drugs to antibodies and penetrating into cancer tissues due to the size of the conjugates. Aptamers are garnering much attention as an alternative to satisfying the unmet needs of antibodies, showing steady demands in various application areas.
-
-
A broad range of target
(protein, small molecule, etc.)
-
-
Excellent binding affinity
(high specificity)
-
-
Safe materials
(low toxicity)
-
-
Easily mass-produced
(low price)
Securing growth momentum
Natural nucleoside-based aptamers in early days had limitations in commercialization due to the lack of diversity and biostability. However, since the aptamers with significantly improved druggability using modified nucleosides were introduced, the technological foundation for commercialization has been laid. In addition, there has been a growing number of research articles on aptamer technology since the original patent expired, providing sufficient momentum for the development of commercial purposes.
- SELEX was firstly developed by Professor Larry Gold from the University of Colorado in 1990.
- Aptamers has been in the limelight since Macugen was successfully launched as the first aptamer drug in 2005.
- Many succeeding products initiated their clinical trial stage, but Macugen lost its competitiveness in the market and the succeeding pipelines such as Fovista ended in failure at the clinical stage.
- Momentum for commercialization is secured through the expiration of the original technology patent and the development of new modified nucleic acid technology
Our Technology Platform
Aptamer Sciences has made our efforts to develop technologies which effectively discover high quality aptamers, technologies which optimize the discovered aptamers to serve the purpose of application, and to build the technology platform with a distinctive aptamer archive.
Aptamer Discovery Technology
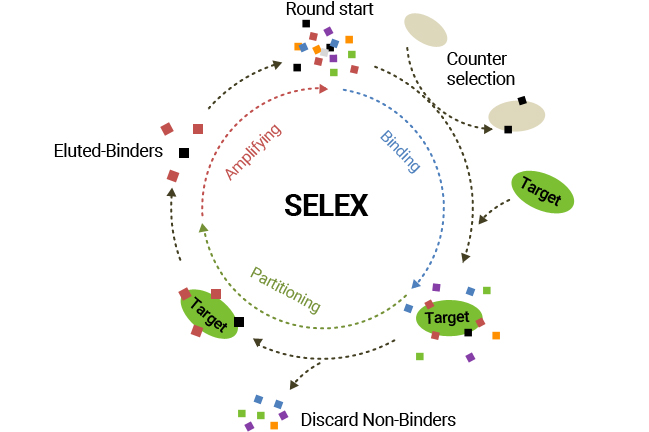
SELEX is a combinatorial technique for discovering aptamers which bind to target molecules with high affinity and specificity; briefly, combining target molecules with nucleic acid libraries with diversity, removing unbound nucleic acids, and collecting the remaining nucleic acids which bind to targets.
PCR amplification and repeating above process make it possible to enrich the only nucleic acids with high affinity to target molecules. The final aptamer clones are selected by sequencing and analyzing their affinity to a target. Since SELEX was firstly developed by Professor Larry Gold at the University of Colorado in 1990, a number of aptamers against a variety of target molecules have been discovered.
Next-generation Aptamer Discovery Technology with established independent Aptamer Platform Technology which are suitable for developing application.
- 01
-
SELEX
Technology to discover high quality aptamers from a DNA library with improved binding affinity for target molecules by increasing the diversity and hydrophobicity of the library. (Binding affinity ≤ 20 nM, Binding time > 30 minutes)
- 02
-
ViroSELEX
Technology to improve the applicability of aptamers by displaying targets on the virus surface, mimicking the original environment. Technology to specialize in discovering high-target specific aptamers for membrane proteins that are available for therapeutic targets.
- 03
-
NGS analysis
A sequencing-based aptamer selection technique analyzing sequence patterns and structural similarities, and technology to increase possibility to obtain various clones.
Aptamer Optimization Technology
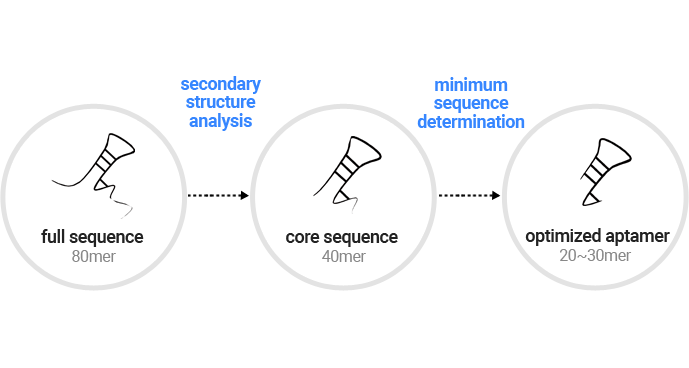
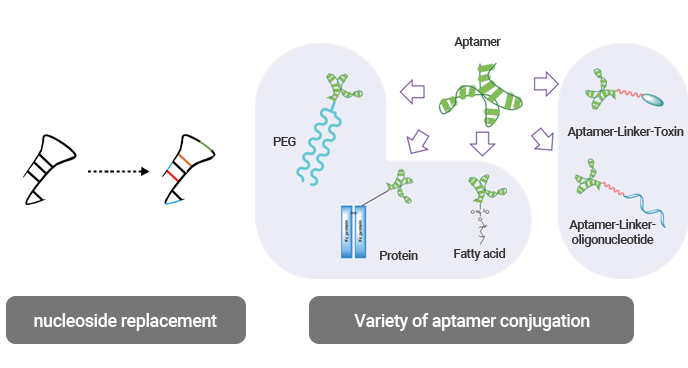
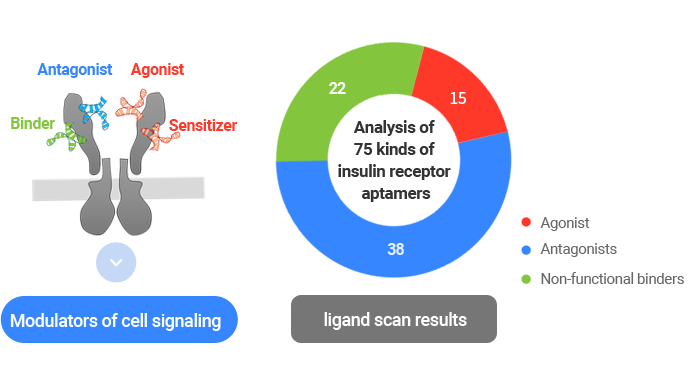
Selected aptamers will go through the optimization process to increase their utility for application. This technology is essential in terms of developing therapeutics and early-stage diagnostic products. Aptamer Sciences is striving to optimize aptamers to have their best structures and efficacy by allowing them to go through “truncation,” “lead optimization,” “ligand scan,” and “aptamer pair discovery”.
-
Truncation
-
Lead optimization
-
Ligand scan
-
Aptamer pair discovery
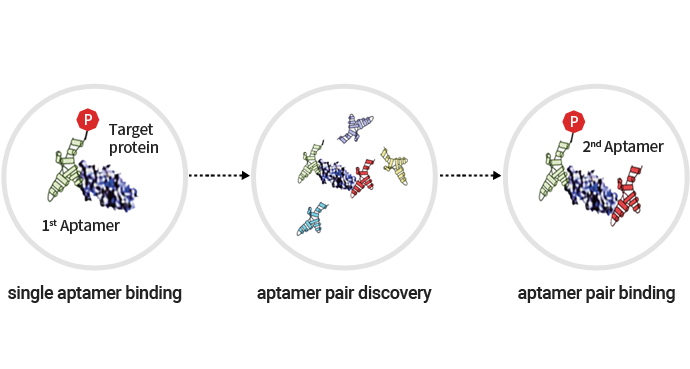
Aptamer Archive
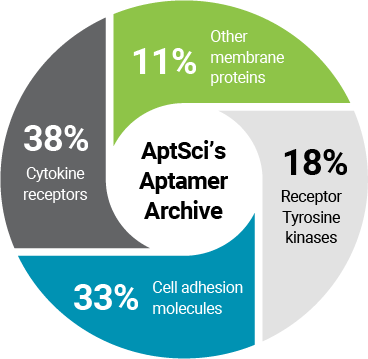
Aptamer Sciences has an archive of selective and high-affinity aptamers for more than 250 membrane receptor proteins which are valid for therapeutic targets. Drug candidates for the development of innovative aptamer-based therapeutics are identified and selected through the optimization process.
If you are interested in the aptamer archive, please click below to contact us.

